Homomorphic Encryption: A Game-Changer for Data Privacy

4.3 out of 5
| Language | : | English |
| File size | : | 5273 KB |
| Text-to-Speech | : | Enabled |
| Screen Reader | : | Supported |
| Enhanced typesetting | : | Enabled |
| Print length | : | 142 pages |
In the ever-evolving digital landscape, protecting sensitive data has become paramount. Homomorphic encryption, a groundbreaking cryptographic technique, has emerged as a game-changer in the quest for privacy and security. By enabling computations on encrypted data without decryption, homomorphic encryption empowers us to unlock new possibilities in data protection and privacy-preserving computation.
In this comprehensive article, we will delve into the fascinating world of homomorphic encryption, exploring its fundamental concepts, practical applications, and far-reaching implications for various industries. From healthcare to finance and beyond, homomorphic encryption is poised to revolutionize the way we handle and protect sensitive information in the digital age.
The Essence of Homomorphic Encryption
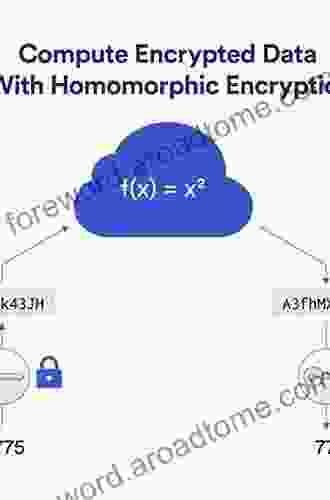
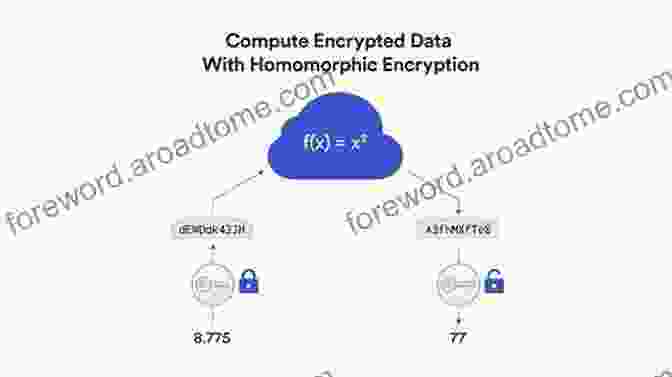
Homomorphic encryption is a transformative cryptographic technique that allows computations to be performed on encrypted data without the need for decryption. This remarkable property empowers us to process and analyze sensitive information while keeping it secure and private.
Unlike traditional encryption methods, homomorphic encryption preserves the algebraic properties of the encrypted data. This means that mathematical operations, such as additions, multiplications, and comparisons, can be performed directly on the encrypted data, and the results will remain encrypted and valid.
Key Properties of Homomorphic Encryption
- Homomorphic Addition: Addition can be performed on encrypted data, resulting in an encrypted representation of the sum.
- Homomorphic Multiplication: Multiplication can also be performed on encrypted data, resulting in an encrypted representation of the product.
- Multi-Party Computation: Multiple parties can collaborate on computations on encrypted data without revealing their private inputs.
- Privacy Preserving: The encrypted data remains confidential and cannot be decrypted by unauthorized parties, ensuring the privacy of sensitive information.
Practical Applications of Homomorphic Encryption
The transformative potential of homomorphic encryption extends across a wide range of industries, enabling groundbreaking applications that preserve privacy and unlock new possibilities.
Healthcare
Homomorphic encryption safeguards sensitive medical data, allowing researchers to analyze encrypted patient information for disease diagnosis, treatment optimization, and personalized medicine. It empowers healthcare providers with the ability to collaborate on patient care while maintaining privacy and confidentiality.
Finance
In the financial sector, homomorphic encryption secures financial transactions, enables fraud detection on encrypted data, and facilitates secure and transparent audits. It protects sensitive financial information, such as account balances and transaction details, from unauthorized access.
Cloud Computing
Homomorphic encryption empowers cloud service providers to offer secure data storage and computation services. It enables clients to encrypt their data before outsourcing it to the cloud, allowing computations to be performed on the encrypted data in the cloud without compromising its security.
Blockchain
Homomorphic encryption enhances the privacy and scalability of blockchain-based systems. It allows smart contracts to operate on encrypted data, ensuring the confidentiality of sensitive transaction data and enabling the development of privacy-preserving decentralized applications.
The Book: Homomorphic Encryption and Applications
For those seeking an in-depth understanding of homomorphic encryption and its applications, we highly recommend the book "Homomorphic Encryption and Applications", published by SpringerBriefs in Computer Science.
This comprehensive book provides a thorough exploration of the fundamental concepts, algorithms, and applications of homomorphic encryption. It delves into the latest advances and provides insightful case studies that showcase the practical implementation of homomorphic encryption in various domains.
Homomorphic encryption is a transformative technology that unlocks a new era of privacy and security in the digital age. Its ability to perform computations on encrypted data without decryption empowers us to safeguard sensitive information, revolutionize data analysis, and enable groundbreaking applications across industries. As homomorphic encryption continues to evolve, we can expect to witness even more groundbreaking breakthroughs and applications that will shape the future of privacy and security in the digital world.
4.3 out of 5
| Language | : | English |
| File size | : | 5273 KB |
| Text-to-Speech | : | Enabled |
| Screen Reader | : | Supported |
| Enhanced typesetting | : | Enabled |
| Print length | : | 142 pages |
Do you want to contribute by writing guest posts on this blog?
Please contact us and send us a resume of previous articles that you have written.
 Book
Book Novel
Novel Page
Page Chapter
Chapter Text
Text Story
Story Genre
Genre Reader
Reader Library
Library Paperback
Paperback E-book
E-book Magazine
Magazine Newspaper
Newspaper Paragraph
Paragraph Sentence
Sentence Bookmark
Bookmark Shelf
Shelf Glossary
Glossary Bibliography
Bibliography Foreword
Foreword Preface
Preface Synopsis
Synopsis Annotation
Annotation Footnote
Footnote Manuscript
Manuscript Scroll
Scroll Codex
Codex Tome
Tome Bestseller
Bestseller Classics
Classics Library card
Library card Narrative
Narrative Biography
Biography Autobiography
Autobiography Memoir
Memoir Reference
Reference Encyclopedia
Encyclopedia Mike Fougnie
Mike Fougnie Ed Samuel
Ed Samuel Elena Garcia
Elena Garcia Fr Mark S Lawlor
Fr Mark S Lawlor Mike Range
Mike Range Mark Osteen
Mark Osteen Shyne Coleman
Shyne Coleman Dr Patrick Crocker
Dr Patrick Crocker Ellen Dietrick
Ellen Dietrick John Thorndike
John Thorndike Peter Wayner
Peter Wayner Elaine Costello
Elaine Costello Robert Taibbi
Robert Taibbi Elaine Shannon
Elaine Shannon Melanie Channell
Melanie Channell Rob Halford
Rob Halford Katrin Van Dam
Katrin Van Dam Edward F Edinger
Edward F Edinger Jag Bhalla
Jag Bhalla Elaine Howard Ecklund
Elaine Howard Ecklund
Light bulbAdvertise smarter! Our strategic ad space ensures maximum exposure. Reserve your spot today!

 Chadwick PowellPlan for the Rapid Start of Ketosis: Unleash Optimal Health and Transform...
Chadwick PowellPlan for the Rapid Start of Ketosis: Unleash Optimal Health and Transform...
 James GrayBucky Fuller and the Sacred Geometry of Nature: Unlocking the Secrets of the...
James GrayBucky Fuller and the Sacred Geometry of Nature: Unlocking the Secrets of the... Dwight BlairFollow ·6.3k
Dwight BlairFollow ·6.3k Marc FosterFollow ·6.7k
Marc FosterFollow ·6.7k Kenzaburō ŌeFollow ·5.2k
Kenzaburō ŌeFollow ·5.2k Ezekiel CoxFollow ·14.7k
Ezekiel CoxFollow ·14.7k David PetersonFollow ·6.9k
David PetersonFollow ·6.9k Rubén DaríoFollow ·10.3k
Rubén DaríoFollow ·10.3k Mario SimmonsFollow ·12.2k
Mario SimmonsFollow ·12.2k Edmund HayesFollow ·15.7k
Edmund HayesFollow ·15.7k

 Reginald Cox
Reginald CoxUnveiling the Extraordinary Life of It Israel Birthday...
A Captivating Narrative of...

 Glenn Hayes
Glenn HayesUnveiling the Enchanting Tapestry of "Tales From The...
Are you ready to step...

 Robert Louis Stevenson
Robert Louis StevensonUnlock the Incredible Mental Benefits of Berries:...
As the sun...

 Edwin Cox
Edwin CoxUnlock the Secrets of Terrain with the Army Map Reading...
Embark on an adventure into the untamed...
4.3 out of 5
| Language | : | English |
| File size | : | 5273 KB |
| Text-to-Speech | : | Enabled |
| Screen Reader | : | Supported |
| Enhanced typesetting | : | Enabled |
| Print length | : | 142 pages |