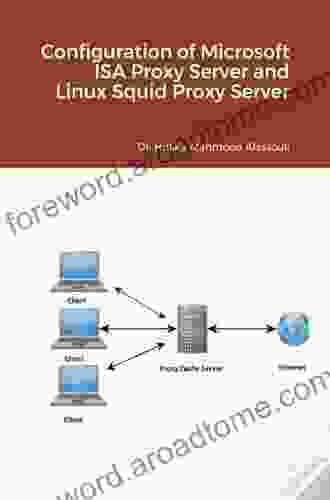
Mastering Proxy Server Configuration: Unleash the Power of Microsoft ISA Proxy Server and Linux Squid Proxy Server

In today's interconnected digital landscape, securing and optimizing your network infrastructure is paramount. Proxy servers play a crucial role in safeguarding your network from external threats, enhancing performance, and controlling access to online resources. This comprehensive guide will delve into the intricate world of proxy server configuration, providing a step-by-step approach to harnessing the capabilities of Microsoft ISA Proxy Server and Linux Squid Proxy Server.
4.4 out of 5
| Language | : | English |
| File size | : | 761 KB |
| Text-to-Speech | : | Enabled |
| Screen Reader | : | Supported |
| Enhanced typesetting | : | Enabled |
| Print length | : | 40 pages |
Chapter 1: Understanding Proxy Servers
Before embarking on the configuration process, it's essential to establish a solid understanding of proxy servers and their multifaceted functionality. This chapter will provide a thorough overview of:
- The fundamentals of proxy servers and their role in network management
- Key benefits and applications of proxy servers, including web filtering, content security, and access control
- Different types of proxy servers and their respective advantages and disadvantages
Chapter 2: Microsoft ISA Proxy Server Configuration
Microsoft ISA Proxy Server is a robust and feature-rich solution for enhancing network security and performance. This chapter will guide you through the detailed steps of ISA Proxy Server configuration, covering:
- Installing and configuring the ISA Proxy Server software
- Configuring web filtering rules to control access to specific websites and content
- Establishing content security policies to protect your network from malicious content
- Implementing access control measures to restrict access to certain websites and applications
- Monitoring and troubleshooting ISA Proxy Server to ensure optimal performance and security
Chapter 3: Linux Squid Proxy Server Configuration
Linux Squid Proxy Server is an open-source and highly customizable solution for proxy server deployment. This chapter will provide comprehensive instructions for configuring Squid Proxy Server on a Linux system, including:
- Installing and configuring the Squid Proxy Server software
- Configuring web filtering rules using Squid's access control lists
- Establishing content security measures through Squid's caching and blacklisting capabilities
- Implementing access control policies to restrict access to specific websites and applications
- Monitoring and troubleshooting Squid Proxy Server to ensure optimal performance and security
Chapter 4: Advanced Proxy Server Configuration
This chapter will delve into advanced proxy server configuration techniques, empowering you to fine-tune your proxy server settings for maximum efficiency and security. You will learn:
- Techniques for optimizing proxy server performance, including caching strategies and load balancing
- Methods for enhancing security through SSL/TLS encryption and authentication mechanisms
- Best practices for monitoring and troubleshooting proxy servers to proactively address issues
- Advanced configuration options for customizing proxy server behavior to meet specific requirements
Chapter 5: Case Studies and Real-World Applications
To solidify your understanding of proxy server configuration, this chapter will present real-world case studies and practical applications. You will explore:
- Examples of how companies have successfully implemented proxy servers to enhance security and improve network efficiency
- Case studies demonstrating the use of proxy servers for content filtering, access control, and web optimization
- Practical tips and best practices for deploying proxy servers in various network environments
Mastering proxy server configuration is an essential skill for network administrators and security professionals. This comprehensive guide has provided a thorough understanding of proxy servers and detailed instructions for configuring Microsoft ISA Proxy Server and Linux Squid Proxy Server. By implementing the techniques and strategies outlined in this guide, you can effectively enhance your network security, improve performance, and gain greater control over your network resources.
Embrace the power of proxy servers today and unlock the full potential of your network infrastructure.
4.4 out of 5
| Language | : | English |
| File size | : | 761 KB |
| Text-to-Speech | : | Enabled |
| Screen Reader | : | Supported |
| Enhanced typesetting | : | Enabled |
| Print length | : | 40 pages |
Do you want to contribute by writing guest posts on this blog?
Please contact us and send us a resume of previous articles that you have written.
 Book
Book Novel
Novel Page
Page Chapter
Chapter Text
Text Story
Story Genre
Genre Reader
Reader Library
Library Paperback
Paperback E-book
E-book Magazine
Magazine Newspaper
Newspaper Paragraph
Paragraph Sentence
Sentence Bookmark
Bookmark Shelf
Shelf Glossary
Glossary Bibliography
Bibliography Foreword
Foreword Preface
Preface Synopsis
Synopsis Annotation
Annotation Footnote
Footnote Manuscript
Manuscript Scroll
Scroll Codex
Codex Tome
Tome Bestseller
Bestseller Classics
Classics Library card
Library card Narrative
Narrative Biography
Biography Autobiography
Autobiography Memoir
Memoir Reference
Reference Encyclopedia
Encyclopedia George A Peters
George A Peters Tom Ashe
Tom Ashe Dylan Robinson
Dylan Robinson Earl Martin
Earl Martin E B Moore
E B Moore Drew Kasch
Drew Kasch Edgar Rothermich
Edgar Rothermich Ginny Smith
Ginny Smith Manuel Maria Di Gioia
Manuel Maria Di Gioia Elizabeth Lonseth
Elizabeth Lonseth Peter A Morgan
Peter A Morgan Eileen Mcdargh
Eileen Mcdargh Lisa Whillock Ellis
Lisa Whillock Ellis Jackie Hunt Christensen
Jackie Hunt Christensen Eleanor Foster
Eleanor Foster Graham T Richardson
Graham T Richardson Fr Mark S Lawlor
Fr Mark S Lawlor Dr Med Susanne Esche Belke
Dr Med Susanne Esche Belke Pamela Wartian Smith
Pamela Wartian Smith Dr Web Links
Dr Web Links
Light bulbAdvertise smarter! Our strategic ad space ensures maximum exposure. Reserve your spot today!

 Herman MitchellEmbrace the Power of Elemental Healing: Unlock Your Inner Healer with "Energy...
Herman MitchellEmbrace the Power of Elemental Healing: Unlock Your Inner Healer with "Energy...
 Maurice ParkerThe Great Physician's Rx for Weight Loss: Transform Your Health and Reclaim...
Maurice ParkerThe Great Physician's Rx for Weight Loss: Transform Your Health and Reclaim... Aleksandr PushkinFollow ·13.4k
Aleksandr PushkinFollow ·13.4k Jim CoxFollow ·15.8k
Jim CoxFollow ·15.8k Bruce SnyderFollow ·6.7k
Bruce SnyderFollow ·6.7k Marc FosterFollow ·6.7k
Marc FosterFollow ·6.7k Jermaine PowellFollow ·13.1k
Jermaine PowellFollow ·13.1k Avery SimmonsFollow ·6.4k
Avery SimmonsFollow ·6.4k Everett BellFollow ·19k
Everett BellFollow ·19k John GrishamFollow ·2.3k
John GrishamFollow ·2.3k

 Reginald Cox
Reginald CoxUnveiling the Extraordinary Life of It Israel Birthday...
A Captivating Narrative of...

 Glenn Hayes
Glenn HayesUnveiling the Enchanting Tapestry of "Tales From The...
Are you ready to step...

 Robert Louis Stevenson
Robert Louis StevensonUnlock the Incredible Mental Benefits of Berries:...
As the sun...

 Edwin Cox
Edwin CoxUnlock the Secrets of Terrain with the Army Map Reading...
Embark on an adventure into the untamed...
4.4 out of 5
| Language | : | English |
| File size | : | 761 KB |
| Text-to-Speech | : | Enabled |
| Screen Reader | : | Supported |
| Enhanced typesetting | : | Enabled |
| Print length | : | 40 pages |